Heartbleed – I think now it’s not a new name for you, as every informational website, Media and Security researchers are talking about probably the biggest Internet vulnerability in recent history. It is a critical bug in the OpenSSL's implementation of the TLS/DTLS heartbeat extension that allows attackers to read portions of the affected server’s memory, potentially revealing users data, that the server did not intend to reveal.
After the story broke online, websites around the world flooded with the heartbleed articles, explaining how it works, how to protect, and exactly what it is. Yet many didn’t get it right. So based on the queries of Internet users, we answered some frequently asked questions about the bug.
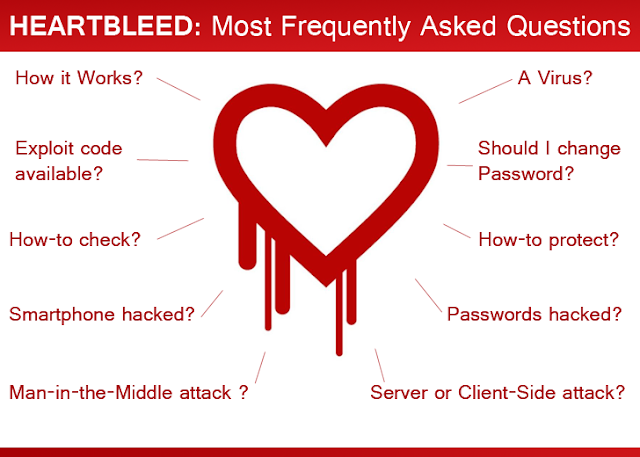
1.) IS HEARTBLEED A VIRUS?
Absolutely NO, It's not a virus. As described in our previous article, The Heartbleed bug is a vulnerability resided in TLS heartbeat mechanism built into certain versions of the popular open source encryption standard OpenSSL, a popular version of the Transport Layer Security (TLS) protocol.
2.) HOW IT WORKS?
For SSL to work, your computer needs to communicate to the server via sending 'heartbeats' that keep informing the server that client (computer) is online (alive).
Heartbleed attack allows an attacker to retrieve a block of memory of the server up to 64kb in response directly from the vulnerable server via sending the malicious heartbeat and there is no limit on the number of attacks that can be performed. [Technically Explained by Rahul Sasi on Garage4hackers]
It opens doors for the cyber criminals to extract sensitive data directly from the server's memory without leaving any traces.
No, it has nothing to deal with a Man-in-the-Middle (MitM) attack. But using Heartbleed attack, one can manage to obtain the private encryption key for an SSL/TLS certificate and could set up a fake website that passes the security verification.
An attacker could also decrypt the traffic passing between a client and a server i.e. Perfect man-in-the-middle attack on HTTPS connection.
4.) IS IT A CLIENT SIDE OR SERVER SIDE VULNERABILITY?
TLS heartbeats can be sent by either side of a TLS connection, so it can be used to attack clients as well as servers. An Attacker can obtain up to 64K memory from the server or client as well that uses an OpenSSL implementation vulnerable to Heartbleed (CVE-2014-0160).
Researcher estimated two-thirds of the world's servers i.e. half a million servers are affected by the Heartbleed Bug, including websites, email, and instant messaging services.
Video Explanation:
5.) HOW HEARTBLEED AFFECTS SMARTPHONES?
Smartphone is the best practical example of Client side attacks.
All versions of Android OS include outdated versions of OpenSSL library, but only Android 4.1.1 Jelly Bean has the vulnerable heartbeat feature enabled by default. Blackberry also confirmed that some of its products are vulnerable to Heartbleed bug, whereas Apple's iOS devices are not affected by OpenSSL flaw.
Google had patched the affected version Android 4.1.1, but it will take long time to deliver updated Android version to the end Smartphone users as updates to majority handsets are controlled by phone manufacturers and wireless carriers. Until users running the affected versions are vulnerable to the attacks, and hackers will definitely take advantage of this public disclosure.
6.) WHAT ELSE COULD BE VULNERABLE TO HEARTBLEED?
IP phones, Routers, Medical devices, Smart TV sets, embedded devices and millions of other devices that rely on the OpenSSL to provide secure communications could also be vulnerable to Heartbleed bug, as it is not expected for these devices to get the updates soon from Google’s Android partners.
Yesterday, Industrial Control Systems-CERT also warned the critical infrastructure organizations (like energy, utilities or financial services companies) to beef-up their systems in order to defend against the Heartbleed attacks.
7.) WHO IS RESPONSIBLE FOR HEARTBLEED?
We actually can't blame anyone developer, specially who are contributing to Open Source projects without money motivations.
Dr. Robin Seggelmann, a 31-year-old German developer who actually introduced the Heartbeat concept to OpenSSL on New Year's Eve, 2011, says it was just a programming error in the code that unintentionally created the “Heartbleed” vulnerability.
"In one of the new features, unfortunately, I missed validating a variable containing a length", went undetected by the code reviewers and everyone else for over two years. He claimed 'I did so unintentionally'.
8.) WHO HAS EXPLOITED THIS BUG YET?
Bloomberg accused the National Security Agency (NSA) of knowing the Heartbleed bug for the last two years. Not even this, the report says the agency was using it continuously to gain information instead of disclosing it to the OpenSSL developers. But if it is so, then this would be one of the biggest developments in the history of wiretapping ever. However, the agency denied it saying NSA was not aware of Heartbleed until it was made public.
But when it comes to exploit any known vulnerability, then Hackers are most likely to be top on the list. As the flaw was so widely spread that it affected half a million websites worldwide, so after the public disclosure, the cybercriminals could reach the sites to steal credentials, passwords and other data, before the site operators apply the freely available patch.
There are multiple Proof-of-concept exploits available for the Heartbleed flaw:
9.) CHANGING ACCOUNT PASSWORDS CAN SOLVE THE ISSUE?
Not exactly, as Heartbleed attack has the ability to leak anything from the server including your passwords, credit card details or any kind of personal information. But, in order to protect your online accounts you should at least change your passwords immediately for the sites that resolved the issue and for the sites not affected by the bug as well, just to make sure that you are safe.
First of all check if the sites you use every day on an individual basis are vulnerable to Heartbleed bug or not using following services or apps:, and if you're given a red flag, avoid the site for now.
- http://filippo.io/Heartbleed/
- Provensec Scanner
- GlobalSign SSL Configuration Checker
- ADTsys Checker
- The easiest way to keep you safe is to use a new add-on to the Chrome browser, Chromebleed, created by security researcher, Jamie Hoyle.
- To check whether your Android devices are safe or not, you can install the Bluebox Heartbleed Scanner available on the Google Play Store. The Bluebox Heartbleed Scanner looks for apps installed on your device that have bundled their own version of OpenSSL and the scanner also checks the version of the library and whether heartbeat is enabled or not.
Well, nobody is sure at this point, because Heartbleed is stealthy as it leaves no traces behind and here the matter goes worse.
You may never know if you have been hacked using the flaw or not. This means that there is no way to tell if your information was stolen previously from a site or a service that has now fixed it.
But if you haven't change the password to the popular sites yet, then yes, your password and financial information are still widely open to cybercriminals and other spying agencies.
10.) WHAT SHOULD I DO TO PROTECT MYSELF?
First of all DON'T PANIC. You have to change your password everywhere, assuming that it was all vulnerable before, just to make sure that you are now safe. But hold on... If some sites are still affected by the flaw then your every effort is useless, as it’s up to the site to first fix the vulnerability as soon as possible , because changing the password before the bug is fixed could compromise your new password as well.
If you own a vulnerable SSL Service, then you are recommended to:

If you own a vulnerable SSL Service, then you are recommended to:
- Upgrade the OpenSSL version to 1.0.1g
- Request revocation of the current SSL certificate
- Regenerate your private key
- Request and replace the SSL certificate
Don't reuse any old passwords and it is good practice to use two-factor authentication, which means with the password, the account requires a freshly generated pass code that shows up only on your personal smartphone, before getting into certain sites.













0 comments:
Post a Comment